Once you have an OAuth 2.0 implementation, you can optionally configure OAuth-based App Flip, which allows your Android users to more quickly link their accounts in your authentication system to their Google accounts. The following sections describe how to design and implement App Flip for your Cloud-to-cloud integration.
Design guidelines
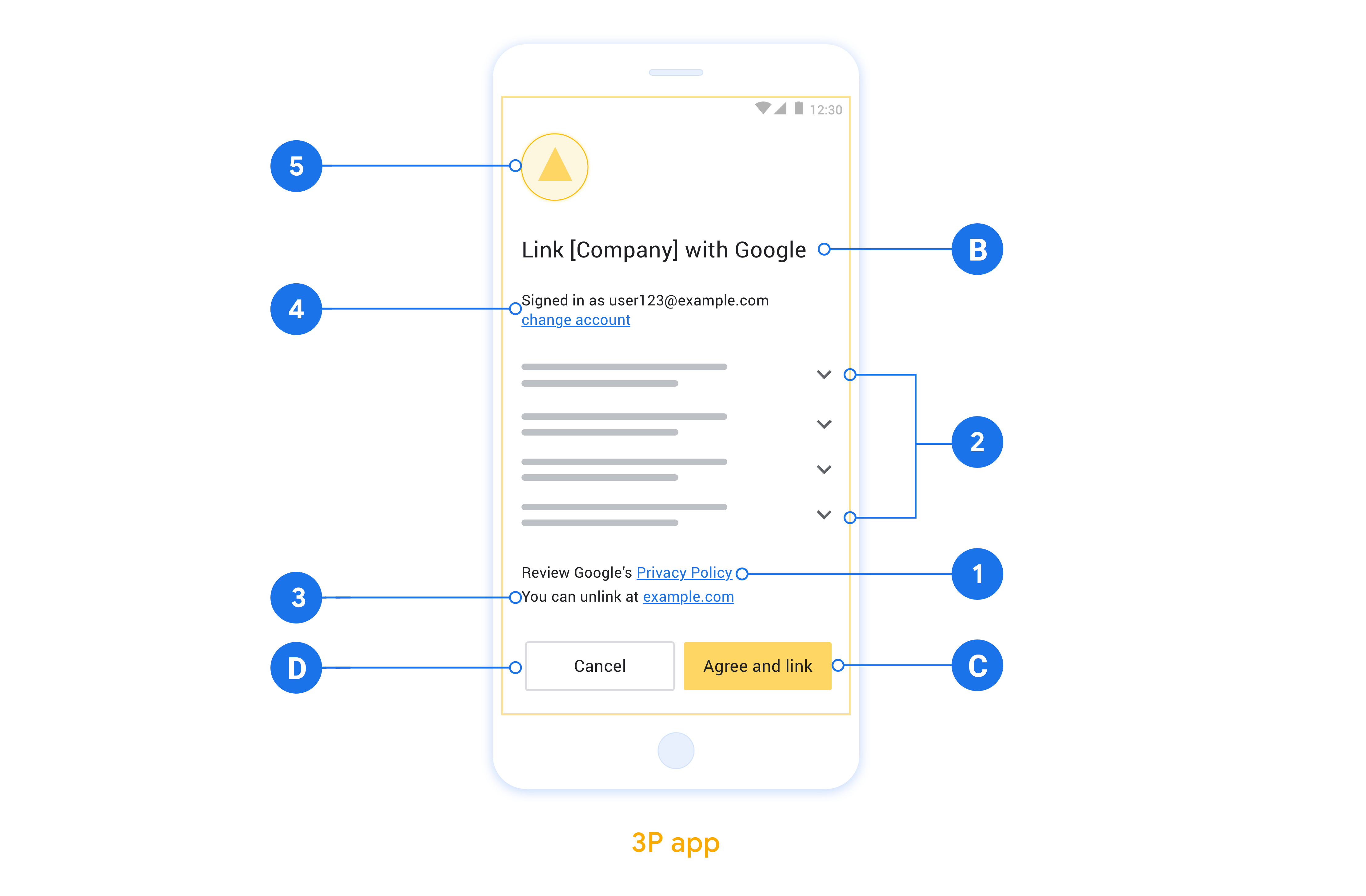
This section describes the design requirements and recommendations for the App Flip account linking consent screen. After Google calls your app, your app displays the consent screen to the user.
Requirements
- You must have a Google authorization statement such as "Once linked, Google will have permission to control your devices."
- You must communicate that the user's account is being linked to Google, not to a specific Google product, such as Google Home or Google Assistant.
- You must state a clear call-to-action on your consent screen and use the wording "Agree and link" for linking action. This is because users need to understand what data they're required to share with Google to link their accounts.
- You must provide a way for users to go back or cancel, if they choose not to link. Use the wording "Cancel" for the cancel action.
- You must implement this workflow: After clicking "Agree and link", you must show linking success and redirect the user back to the Google Home app automatically. The user should now see the linked device on the Google Home app with your action. After clicking "Cancel" you should redirect the user back to the Google Home app.
Recommendations
We recommend that you do the following:
Display Google's Privacy Policy. Include a link to Google's Privacy Policy on the consent screen.
Data to be shared. Use clear and concise language to tell the user what data of theirs Google requires and why.
Ability to unlink. Offer a mechanism for users to unlink, such as a URL to their account settings on your platform. Alternatively, you can include a link to Google Account where users can manage their linked account.
Ability to change user account. Suggest a method for users to switch their account(s). This is especially beneficial if users tend to have multiple accounts.
- If a user must close the consent screen to switch accounts, send a recoverable error to Google so the user can sign in to the desired account with OAuth linking and the implicit flow.
Include your logo. Display your company logo on the consent screen. Use your style guidelines to place your logo. If you wish to also display Google's logo, see Logos and trademarks.
Set up for OAuth-based App Flip
The following sections describe the prerequisites for OAuth-based App Flip and how to configure your App Flip project in the Google Home Developer Console.
Create a Cloud-to-cloud integration and set up an OAuth 2.0 server
Before you can configure App Flip, you need to do the following:
- Set up an OAuth 2.0 server. For more information about setting up an OAuth server, see Implement an OAuth 2.0 server.
- Create a Cloud-to-cloud integration. To create an integration, follow the instructions in Create a Cloud-to-cloud integration.
Configure App Flip in the Developer Console
The following section describes how to configure App Flip in the Developer Console.
- Fill out all the fields under OAuth Client information. (If App Flip isn't supported, regular OAuth is used as a fallback.)
- Under Use your app for account linking(optional), check Enable for iOS.
- Fill out the Universal Link field. For more information about universal links, see Allowing Apps and Websites to Link to your Content.
- If you want to optionally configure your client, add scopes and click Add scope under Configure your client (optional).
- Click Save.
You can now continue to the next section to implement App Flip in your iOS or Android app.
Implement App Flip in your native apps
To implement App Flip, you need to modify the user authorization code in your app to accept a deep link from Google.
Test App Flip on your device
Now that you've created a Cloud-to-cloud integration and configured App Flip on the console and in your app, you can test App Flip on your mobile device. You can use the Google Home app to test App Flip.
To test App Flip from the Google Home app, follow these steps:
- Go to the Developer Console and select your project.
- Go to Cloud-to-cloud > Test.
- Trigger the account linking flow from the Home app:
- Open the Google Home app (GHA).
- Click the + button.
- Click Set up device.
- Click Have something already set up?
- Select your Cloud-to-cloud integration from the list of providers. It will be prefixed with “[test]” in the list. When you select your [test] integration from the list, it should open your app.
- Verify that your app was launched and begin testing your authorization flow.
